Why This Matters
Previously, applications running on AWS that needed to interact with third-party SaaS platforms relied heavily on API keys — credentials that had to be stored, rotated, and secured. This created operational headaches and increased security risks, especially when keys were accidentally exposed or compromised.
This enhancement streamlines cross-cloud and hybrid deployments by enabling IAM principals (roles and users) to request cryptographically signed JWTs that assert their AWS identity. External services can then verify the authenticity of these tokens and grant access accordingly, removing the necessity to store sensitive credentials for extended periods.
How It Works
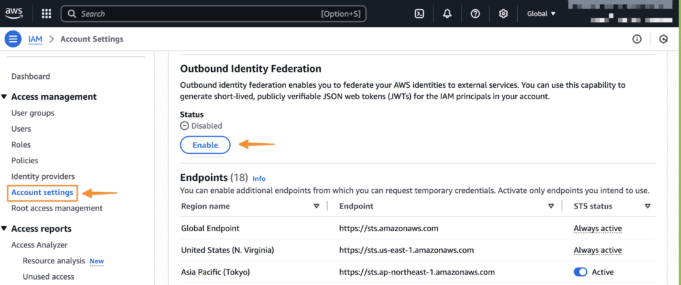
With IAM outbound identity federation, an application can request a short-lived JWT from the AWS Security Token Service (STS) using the GetWebIdentityToken API. The process involves exchanging AWS credentials for a temporary, digitally signed JWT, which acts as proof of the application’s identity to the external service.
Authentication Workflow
| Step | Action | Description |
|---|---|---|
| 1 | Token Request | Application requests a token from AWS STS |
| 2 | JWT Generation | AWS STS returns a signed JWT asserting the application’s identity |
| 3 | Token Presentation | Application presents the JWT to the external service |
| 4 | Verification | External service verifies token authenticity using keys from the JWKS endpoint |
| 5 | Access Grant | Upon successful verification, external service grants access to its resources |
Implementation Guide
Step 1: Enable Outbound Identity Federation
First, enable outbound identity federation in the IAM console within your AWS account settings. This action prompts AWS to generate a unique issuer URL for your account, which hosts the necessary OpenID Connect (OIDC) discovery endpoints.
Step 2: Configure IAM Permissions
The IAM principal must have the sts:GetWebIdentityToken permission to request tokens. Here’s an example policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:GetWebIdentityToken",
"Resource": "*"
}
]
}Step 3: Configure External Service Trust
The external service must be configured to trust and accept tokens issued by your AWS account. This typically involves:
- Identity provider registration: Register your AWS account issuer URL as a trusted identity provider
- Claim validation setup: Configure claim validation, including audience and subject patterns
- Permission mapping: Map token claims to permissions within the external service
Code Examples
Requesting a JWT Token
To obtain a JWT, call the STS GetWebIdentityToken API, specifying parameters such as audience, signing algorithm, and token lifetime. Here’s an example using the AWS SDK for Python (Boto3):
import boto3
sts_client = boto3.client('sts')
response = sts_client.get_web_identity_token(
Audience=['my-app'],
SigningAlgorithm='ES384', # or 'RS256'
DurationSeconds=300
)
jwt_token = response['IdentityToken']
print(jwt_token)This code returns a signed JWT that can be inspected using a JWT parser. The token payload contains standard OIDC claims, along with AWS-specific metadata, including the account ID, organization ID, and principal tags.
Verifying JWT Tokens
External services can verify the token using the issuer URL (found in the iss claim) and the JWKS endpoint. Here’s a Python example demonstrating token verification:
import json
import jwt
import requests
from jwt import PyJWKClient
# Trusted issuers list - obtained from EnableOutboundFederation API response
TRUSTED_ISSUERS = [
"https://EXAMPLE.tokens.sts.global.api.aws", # Add your trusted AWS account issuer URLs here
# Obtained from EnableOutboundFederation API response
]
def verify_aws_jwt(token, expected_audience=None):
"""Verify an AWS IAM outbound identity federation JWT"""
try:
# Get issuer from token
unverified_payload = jwt.decode(token, options={"verify_signature": False})
issuer = unverified_payload.get('iss')
# Verify issuer is trusted
if not TRUSTED_ISSUERS or issuer not in TRUSTED_ISSUERS:
raise ValueError(f"Untrusted issuer: {issuer}")
# Fetch JWKS from AWS using PyJWKClient
jwks_client = PyJWKClient(f"{issuer}/.well-known/jwks.json")
signing_key = jwks_client.get_signing_key_from_jwt(token)
# Verify token signature and claims
decoded_token = jwt.decode(
token,
signing_key.key,
algorithms=["ES384", "RS256"],
audience=expected_audience,
issuer=issuer
)
return decoded_token
except Exception as e:
print(f"Token verification failed: {e}")
return NoneAccess Control and Security
AWS account administrators can use IAM policies to control which IAM principals are authorized to generate tokens. New condition keys enable fine-grained control:
- sts:SigningAlgorithm: Specify which cryptographic signing algorithms are permitted
- sts:IdentityTokenAudience: Control which token audiences can be requested
- sts:DurationSeconds: Set maximum token lifetimes to limit exposure windows
These controls allow security teams to enforce organizational policies while giving developers the flexibility they need to integrate with external services.
Availability and Pricing
| Aspect | Details |
|---|---|
| Cost | Available at no additional cost |
| Regional Availability | All AWS commercial Regions, AWS GovCloud (US) Regions, and China Regions |
| Configuration | Can be enabled in the AWS IAM console |
Key Benefits
- Enhanced security: Eliminates long-term credential storage and reduces risk of credential exposure
- Reduced operational overhead: No more API key rotation, storage, or distribution to manage
- Simplified cross-cloud integration: Standardized JWT approach works with any service that supports OIDC
- Short-lived tokens: Configurable token lifetimes minimize security exposure windows
- Cryptographic verification: External services can independently verify token authenticity without calling back to AWS
- Fine-grained access control: IAM policies provide precise control over who can generate tokens and under what conditions
AWS IAM outbound identity federation represents a significant advancement toward simplified and secure cross-cloud integration. By utilizing JWTs, developers can streamline authentication processes, decrease operational burdens, and improve the overall security of their applications.
For organizations running hybrid or multi-cloud architectures, this feature removes one of the persistent pain points in managing service-to-service authentication. Instead of juggling API keys across different platforms, teams can now leverage their existing AWS IAM infrastructure to securely authenticate to external services.
The no-cost availability across all AWS regions makes this accessible to organizations of any size, and the standards-based approach (OIDC and JWT) ensures compatibility with a wide range of external services. For teams already invested in AWS IAM for access management, this is a natural extension that simplifies their security architecture without introducing new complexity.