In the chaotic landscape of cloud computing, where misconfigurations can snowball into security nightmares, a new open-source tool called cnspec is vying for attention. It promises to bring order to sprawling cloud setups by automating security and compliance checks across clouds, containers, and APIs, offering a unified view of potential vulnerabilities. This is especially relevant now as companies struggle to maintain security across increasingly complex hybrid and multi-cloud environments.
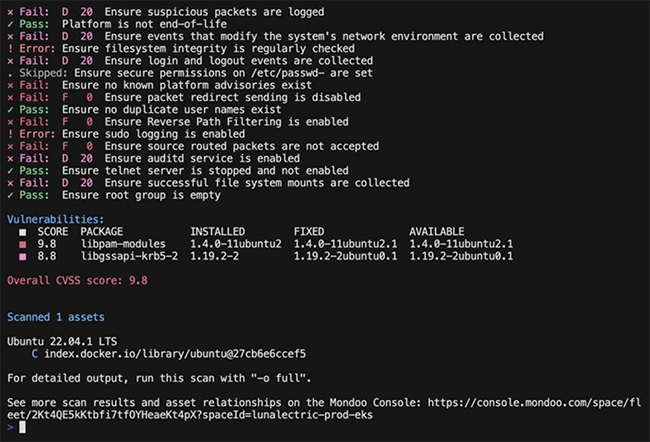
At its heart, cnspec operates as a policy-as-code engine, driven by a security data fabric. This allows users to codify security checks and run them at scale across diverse environments, from public and private clouds to Kubernetes clusters and even SaaS applications. The goal? To catch misconfigurations and vulnerabilities before they become costly breaches.What truly distinguishes cnspec is its extensive reach. It’s not just about scanning AWS, Google Cloud, or Azure accounts. The tool casts a wide net, encompassing:
- Kubernetes clusters and manifests
- Container images and registries
- Server endpoints (Linux, macOS, Windows)
- SaaS platforms like Microsoft 365, Atlassian, and Okta
- Infrastructure-as-code artifacts (Terraform HCL, plan, and state files)
- Network hosts and DNS records
- Version control systems (GitHub, GitLab)
- IoT and OPC-UA devices
- VMware platforms
This breadth allows security professionals to enforce a consistent set of policies across the entire environment, bridging the gap between cloud build pipelines and runtime operations. This comprehensive approach stands in contrast to siloed security tools that address only specific aspects of the infrastructure.
cnspec offers a straightforward entry point: install the tool, run scans, and execute policy checks. For ad-hoc investigations, an interactive shell is available. Out-of-the-box default policies provide a solid foundation, which users can then extend or customize to align with their specific environment and risk profile.
The real power of cnspec lies in its integration capabilities. Connecting it to source control, CI/CD pipelines, registry scanning, runtime monitoring, and asset inventory is crucial for maximizing its effectiveness. While cnspec provides valuable insights, it’s not a silver bullet. It’s a component that enhances, but doesn’t replace, the existing security stack.
For CISOs and security architects, the ability to apply consistent checks across diverse clouds, platforms, and services translates to fewer security gaps and improved alignment between compliance, security operations, and DevSecOps initiatives. By catching issues early in the development lifecycle, cnspec helps shift security left, reducing the cost and complexity of remediation.
The value of integrating security into the development process is paramount. As Alexis Wales, GitHub CISO, notes regarding collaborating with the open-source community, as discussed in a recent Help Net Security article, the collective knowledge and scrutiny of the community can significantly enhance security posture.
cnspec is available for free on GitHub, making it accessible to organizations of all sizes. This aligns with the growing trend of leveraging open-source tools for security, as highlighted in this list of 35 open-source security tools, empowering red teams, SOCs, and cloud security teams.
The open-source nature of cnspec fosters community-driven development and allows users to contribute to its evolution. As organizations grapple with the ever-increasing complexity of cloud security, tools like cnspec that offer visibility, automation, and extensibility will likely play an increasingly important role in maintaining a secure and compliant posture.