Managing authentication credentials securely is one of the most critical challenges in modern cloud architecture. While OAuth 2.0 and OpenID Connect (OIDC) provide robust authentication frameworks, the manual handling of client secrets remains a significant security risk. Let’s explore an elegant automated solution using AWS services that will help you sleep better at night.
How to Secure OIDC Client Secrets: AWS Load Balancer Guide
Traditional approaches to managing OIDC client secrets often involve manual updates and plaintext credential storage – practices that make security professionals cringe. The good news? Elastic Load Balancing combined with AWS’s powerful security services offers a breakthrough solution for automating this critical process.
The Secret Sauce: Automated Rotation Architecture
The magic happens through a clever orchestration of AWS services:
- AWS Secrets Manager acts as your secure vault, storing and managing OIDC credentials
- AWS Lambda functions handle the heavy lifting of secret rotation
- Amazon EventBridge keeps everything running like clockwork
Think of it as your own security automation butler – always vigilant, never sleeping, and following industry best practices to the letter.
Why This Matters: Real-World Impact
Consider this: A single compromised OIDC client secret could give attackers access to your entire application ecosystem. The automated solution eliminates common vulnerabilities like:
- Exposed plaintext credentials in configuration files
- Forgotten or outdated secrets
- Manual rotation errors
- Lack of audit trails
The best part? Once configured, this system runs silently in the background, automatically rotating secrets every 15 minutes if needed. It’s like having a security guard that never takes a coffee break.
Implementation: Your Quick-Start Guide
Getting started is surprisingly straightforward. First, ensure you have:
- An Application Load Balancer with configured listeners
- An OIDC provider account (like Auth0)
- Initial credentials stored in AWS Secrets Manager
The provided CloudFormation template handles the heavy lifting, creating all necessary components and permissions. Think of it as a “security in a box” solution that implements AWS best practices automatically.

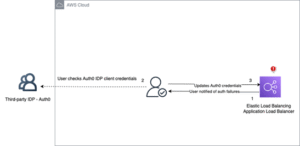
Figure 2: Automated OIDC client secret rotation
Pro tip: While testing, use CloudWatch Logs to monitor the rotation process. It’s like having x-ray vision into your security infrastructure, helping you catch any issues before they become problems.
Ready to take your application security to the next level? Check out the complete deployment guide in the AWS documentation. Your future self will thank you for implementing this robust security solution today.





