Managing sensitive information like API keys, database credentials, and encryption keys, collectively known as secrets, represents a critical security challenge in modern DevOps. According to a technical guide by AWS solutions architects Brendan Paul and Eduardo Patroncinio, organizations typically adopt one of two primary strategies: centralized or decentralized secrets management within their infrastructure deployment pipelines.
The choice between these approaches directly impacts development speed, security enforcement, and operational overhead for teams using Infrastructure as Code (IaC).
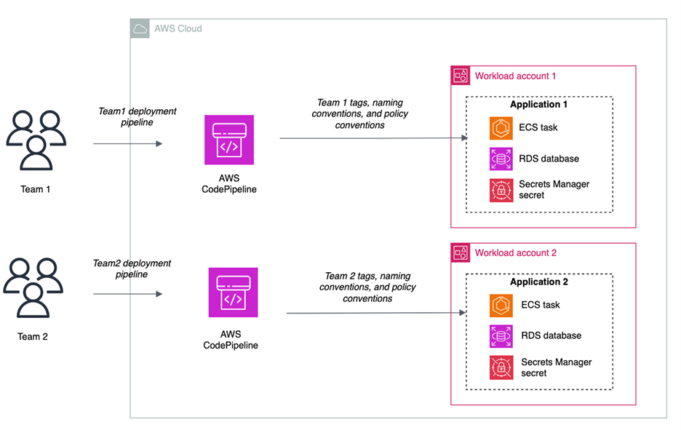
The Decentralized Model
In a decentralized model, individual application teams are responsible for creating and managing their own secrets within their respective accounts.
How It Works
Each development team controls the full lifecycle of their secrets:
- Creates secrets as needed for their applications
- Manages rotation schedules independently
- Defines access controls within their own account scope
- Maintains their own security policies
Advantages
Developer autonomy: Teams can create and update secrets without waiting for central platform engineering approval
Speed and agility: No bureaucratic delays or ticket queues for provisioning credentials
Team flexibility: Developers can innovate and experiment without central bottlenecks
Ownership clarity: Teams have direct responsibility for their security posture
Challenges
Governance difficulty: Enforcing consistent security standards across teams becomes challenging without central oversight
Policy fragmentation: Key rotation policies and access controls may vary widely between teams
Increased complexity: Each team must implement monitoring and auditing independently
Misconfiguration risk: Without standardized approaches, security vulnerabilities are more likely
While teams can still leverage tools like AWS Key Management Service (AWS KMS) to control access, ensuring uniform implementation requires robust monitoring across all accounts.
The Centralized Model
A centralized model entrusts a dedicated platform engineering team with secrets lifecycle management across the organization.
How It Works
A central team maintains shared infrastructure for secrets:
- Maintains a common library of rotation functions
- Defines standardized policies for secret creation and access
- Provides pre-approved, reusable security functions
- Monitors secrets usage across all teams and accounts
Advantages
Consistent security posture: Uniform policies and standards enforced across the entire organization
Reusable functions: Developers leverage pre-approved, secure rotation functions without building from scratch
Enhanced visibility: Central teams can monitor for security findings across all accounts using services like AWS Secrets Manager integrated with AWS Security Hub
Faster remediation: Unified view allows quicker detection and response to potential threats
Compliance simplified: Easier to demonstrate adherence to security frameworks and audit requirements
Challenges
Potential bottleneck: Central teams can become dependencies that slow down development velocity
Reduced autonomy: Individual teams must follow central standards even when they don’t fit specific use cases
Scalability concerns: Central teams must support growing numbers of applications and teams
Context limitations: Platform teams may lack deep understanding of each application’s specific security needs
Security Best Practices for Both Models
Regardless of which model you choose, the AWS architects emphasize implementing least-privilege access within CI/CD pipelines.
Automated Policy Enforcement
Use APIs like the `check-no-new-access` API in AWS IAM Access Analyzer to prevent Infrastructure as Code deployments from inadvertently granting new, overly permissive access to secrets. This automated check acts as a guardrail, ensuring infrastructure changes do not create new security vulnerabilities.
Custom Policy Checks
Organizations can implement custom policy checks to enforce specific security requirements programmatically, such as:
- Mandatory rotation schedules (e.g., every 90 days)
- Required encryption standards
- Access control patterns
- Logging and auditing requirements
Making the Decision
The choice between centralized and decentralized secrets management depends on your organization’s priorities:
Choose decentralized if:
- Developer velocity is the primary concern
- Teams have strong security expertise
- Your organization values team autonomy
- You have robust monitoring across all accounts
Choose centralized if:
- Consistent security posture is critical
- Compliance requirements demand uniform standards
- You need comprehensive visibility across the organization
- Platform engineering teams can scale to support application teams
Hybrid Approaches
Many organizations adopt hybrid models that combine elements of both approaches:
- Central teams provide standardized, optional libraries and templates
- Application teams can use central resources or manage their own with approval
- Security policies are centrally defined but enforcement is distributed
- Monitoring and alerting are centralized while day-to-day management is decentralized
What to Consider
When evaluating your secrets management strategy:
- Audit current practices to identify ownership and potential security gaps
- Define clear roles and responsibilities for secret creation, rotation, and access control
- Implement automated security checks within CI/CD pipelines to enforce least-privilege principles
- Utilize cloud-native monitoring tools to gain visibility into secret usage and access patterns
- Establish standardized processes for rotating secrets regularly to minimize risk windows
Industry Trends
The trend toward platform engineering and “golden paths”—standardized templates for infrastructure deployment—suggests growing preference for centralized governance to ensure security and compliance at scale. However, the need for developer agility continues driving demand for self-service capabilities, requiring organizations to balance central control with team autonomy.
Follow us on Bluesky, LinkedIn, and X to Get Instant Updates