Imagine a shadowy figure, silently slipping past security guards, not by brute force, but by cleverly disguising themselves as someone completely harmless. That’s essentially what’s happening with this new iteration of domain fronting, using Google’s own services as a cloak of invisibility for malicious activity.
Hidden Domain Fronting: Bypassing Security with Google
At Black Hat and DEF CON this year, researchers revealed a shockingly simple yet effective method of bypassing security: leveraging the inherent trust placed in Google’s infrastructure. By mismatching the Server Name Indication (SNI) and the HTTP Host header in HTTPS requests, attackers can redirect traffic intended for, say, google.com, to their own malicious server residing within Google Cloud Platform (GCP).
Think of it like this: you’re expecting a package from Amazon, but a sneaky neighbor intercepts it, reseals it with an Amazon label, and delivers it to their own house. The Amazon truck (Google’s infrastructure) delivers the package, but the contents are far from what you expected.
This technique isn’t just theoretical. Researchers demonstrated its effectiveness against a range of Google services, including YouTube, Chrome update servers, Google Meet, and even GCP endpoints themselves. The implications are staggering. Most organizations rely heavily on Google services; blocking them entirely is often impractical, creating a significant security vulnerability.
How the Attack Works: A Deep Dive
The core of the attack lies in the subtle manipulation of the TLS handshake. The SNI, visible to the network, points to a legitimate Google domain (like google.com). However, the HTTP Host header, hidden within the encrypted traffic, secretly directs the request to the attacker’s server within GCP. This discrepancy allows the attacker to intercept and control the communication.
In their proof-of-concept, researchers used a simple Google Cloud Run function to return a “Hello World!” message. By cleverly setting the Host header to their Cloud Run URL while connecting to google.com, they successfully invoked their malicious function – all while appearing to be just another legitimate Google request.
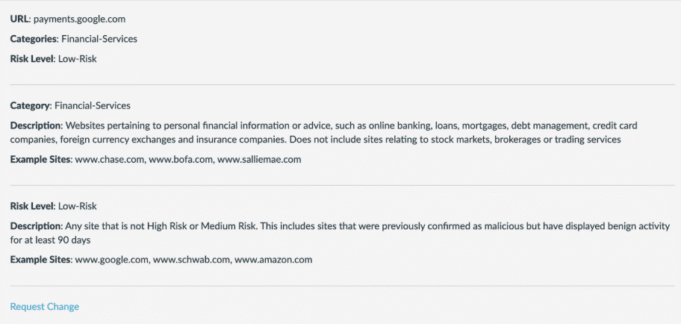
This technique even works against certificate-pinned services, like Snapchat’s API, and sensitive financial endpoints such as payments.google.com, making it incredibly difficult to detect.
The Implications and the Defense
This resurrected domain fronting technique presents a significant challenge to traditional security measures. Simply trusting traffic destined for Google is no longer sufficient. Security teams need to implement deep packet inspection that correlates SNI and HTTP Host headers, looking for discrepancies that indicate malicious redirection.
Furthermore, monitoring unusual backend routing patterns, even within seemingly legitimate Google traffic, is crucial. This requires a shift from perimeter-based security to a more sophisticated approach focusing on deep behavioral analysis.
To make this attack easier to replicate (for ethical penetration testing purposes, of course!), the researchers released an open-source Google Cloud Run redirector at praetorian-inc/google-redirector. This tool simplifies the process of setting up domain fronting infrastructure within GCP.
Beyond the Technical: The Broader Picture
This isn’t just about a clever hack; it highlights a fundamental shift in the cybersecurity landscape. The widespread reliance on cloud services and the trust placed in major tech giants creates new attack vectors. This attack underscores the need for a more nuanced approach to security, moving beyond simple perimeter defenses and embracing advanced techniques like behavioral analysis and anomaly detection.
The future of cybersecurity will likely involve a greater focus on detecting anomalies and unusual behavior, rather than simply relying on blocking known threats. This attack serves as a stark reminder that even the most trusted platforms can be exploited if we don’t adapt our security strategies.
What are your thoughts on this evolving threat landscape? How can organizations effectively mitigate the risks associated with hidden domain fronting?