Shai-hulud 2.0 represents a serious threat to the open-source software supply chain. This malware steals cloud credentials, backdoors NPM packages, and wipes user data. It’s an evolution of the original Shai-hulud worm and possesses enhanced credential theft capabilities, automated supply chain compromise, and destructive functionality.
The attack begins with a compromised NPM package maintainer account, likely gained through phishing. Shai-hulud 2.0 steals credentials for AWS, GCP, Azure, NPM, and GitHub, then uses these to infiltrate cloud-native secret management services. Its ability to automatically backdoor NPM packages is a significant threat, republishing them with malicious payloads that execute upon installation. This creates a wormable vector that can spread rapidly across the NPM ecosystem.
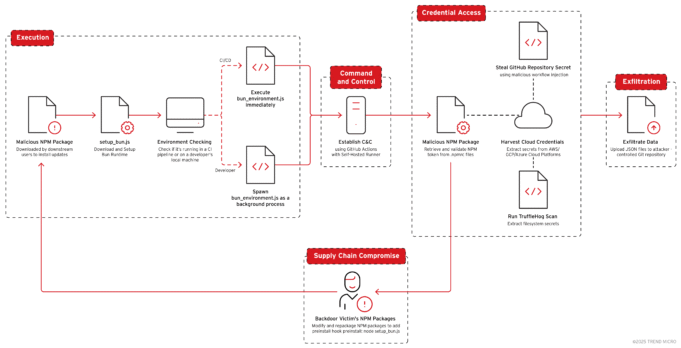
- The attack chain is initiated by a malicious preinstall script, typically named `setup_bun.js`, embedded in an NPM package’s `package.json`. This script executes automatically during the NPM installation process.
- The `setup_bun.js` script functions as a loader, ensuring the presence of the Bun JavaScript runtime on the victim’s system. If Bun is missing, the script downloads and installs it using official Bun installation scripts from `bun.sh`, adding a layer of legitimacy.
- After installing Bun, the script reloads the system PATH to recognize the newly installed executable, using platform-specific techniques. On Windows, it queries the Registry via PowerShell. On Unix-like systems, it sources shell profile files like `.bashrc` and `.zshrc`.
- With Bun installed, the script executes the main malware payload, `bun_environment.js`, using the newly installed runtime.
The `jy1()` function within `bun_environment.js` acts as the malware’s central command center, orchestrating the entire attack sequence. The malware first checks for Continuous Integration/Continuous Delivery (CI/CD) environment variables. If running within a CI/CD pipeline, the malware executes immediately to maximize credential access during build processes. Otherwise, on developer machines, it employs a stealthier approach, spawning a detached background process using `Bun.spawn().unref()` to avoid detection.
The `aL0()` function is where the credential theft and data destruction occur. It targets CI/CD environments and developer workstations to steal credentials for AWS, GCP, Azure, NPM, and GitHub. When authentication fails, the malware initiates destructive commands to wipe user data.
On Linux systems, `aL0()` attempts to establish persistence and disable security controls. It checks for specific processes, attempts privilege escalation via passwordless sudo or Docker exploitation, and disables security controls like `systemd-resolved` and `iptables`. Credential harvesting modules for AWS, Google Cloud Platform, Azure, and GitHub are then instantiated.
The malware targets NPM authentication tokens by searching for `.NPMrc` configuration files and validating the tokens against the `/-/whoami` API endpoint. It establishes command-and-control (C&C) infrastructure by creating a GitHub repository. It verifies GitHub authentication, generates a unique repository name, and uses the GitHub Octokit API to create the repository. It checks for workflow OAuth scope permissions to manage GitHub Actions workflows and runners, requests a runner registration token, and deploys platform-specific runners (Linux, Windows, macOS) to the compromised machine. A GitHub Actions workflow file is created at `.github/workflows/discussion.yaml` that triggers whenever a discussion is created, allowing the attacker to execute arbitrary commands.
As a failsafe, if NPM and GitHub authentication fail, the malware attempts to delete all files in the user’s home directory. The malware collects detailed system information and GitHub credentials to build a comprehensive profile of the victim system. Another GitHub Actions workflow is created to steal all repository secrets, injecting malicious workflow files into each repository accessible to the compromised account. The malicious workflow, disguised as a “Code Formatter,” triggers on every push event, serializing the entire secrets object into a JSON string using the `toJSON()` function and exfiltrating it. The malware monitors the GitHub Actions API to detect when the workflow executes and completes, downloads the exfiltrated secrets from the workflow artifacts, and extracts the `format.json` file.
Shai-hulud 2.0 harvests credentials from AWS, GCP, and Azure, then retrieves secrets from AWS Secrets Manager, GCP Secret Manager, and Azure Key Vault.
For AWS, it uses the built-in credential provider chain, targeting environment variables and configuration files, and containerized environments like ECS and EKS.
For GCP, it targets the Application Default Credentials (ADC) system, checking for the `GOOGLE_APPLICATION_CREDENTIALS` environment variable and the Google Cloud SDK configuration directory.
For Azure, it scans Azure-related environment variables and attempts multiple authentication methods, including Service Principal credentials, certificate-based authentication, and Workload Identity credentials. The malware also uses TruffleHog, an open-source secret scanner, to sweep the victim’s home directory for hardcoded secrets.
The malware aggregates and uploads stolen data to an attacker-controlled Git repository, creating separate JSON files for system metadata (`contents.json`), environment variables (`environment.json`), cloud secrets (`cloud.json`), and TruffleHog scan results (`truffleSecrets.json`).
The malware automatically backdoors every NPM package maintained by the compromised user, republishing them with malicious payloads that run during package installation. This turns trusted packages into vectors for infection. The attack involves discovering all packages owned by the maintainer, downloading their original tarballs, injecting malicious preinstall hooks, bundling the malware installer, and republishing the modified packages. This is done at scale, parallelizing across up to 100 packages at once.
Trend Micro’s Vision One platform detects and blocks the indicators of compromise (IOCs) associated with Shai-hulud 2.0. They provide customers with tailored threat hunting queries, threat insights, and intelligence reports.